Managing Risks
We have put into effect risk management based on our “Crisis Management Project” initiated in 2005 and settled on regulations concerning important risks that could be conceivable in the course of continuing corporate activities.
Preparation for large-scale disasters
We have regulations and a detailed manual detailing the organization, managers, contact system and employee code of conduct for emergencies, that includes coping with large-scale earthquakes or storm and flood damage when a warning is issued as based on The Large-Scale Earthquake Countermeasures Act. We will make endeavor to ensure the safety of our employees, prevent secondary disaster and issue the decision to continue business operations as soon as possible when a disaster happens. Also, the conduct guide for emergencies is distributed among employees as a card that can be carried to raise common knowledge and awareness.
Protection of individual information
We recognize the importance of individual information, and to provide suitable protections for said information we have established “Individual Information Protection Management Rules” and are working toward more comprehensive information management.
Optimization of individual information handling (obtainment, utilization, and provision)
When obtaining individual information, we will make clear the objectives for its use, how it will be obtained, format and listing details, and the individuals responsible for its management. The departments handling the aforementioned information will manage it appropriately in conformance with laws, ordinances, and rules.
Safety measures concerning information leaks
Departments that handle individual information will implement personnel-related, physical, and technological countermeasures in order to prevent unauthorized accessing, leaking, loss, damaging, or falsification of said information.
Respect for rights
We will expeditiously respond to requests for disclosure, correction, and deletion of personal information after confirming that the person making the request is the person in question.
Responses in the event of mishaps
Should a mishap involving individual information occur, we will expeditiously report the incident to those responsible for managing said information, and take appropriate action after consulting with concerned parties for the information in question.
Information Security
Effective utilization of information through digitalization during our corporate activities is indispensable to smooth execution of our business affairs. We not only can share information in-house but also use the internet to collect it from external sources or easily provide it to recipients outside the company.
However, to the extent that this is convenient, there are concerns over the threat posed by infection of classified information with viruses, equipment failures due to disasters, etc. Should mishaps such as leaking of classified information occur, we would lose business opportunities and the confidence of society across the board, and such losses would be expected to be serious. We also bear a great social responsibility in our capacity as a company that handles IC cards and other such technology with a substantial public impact.
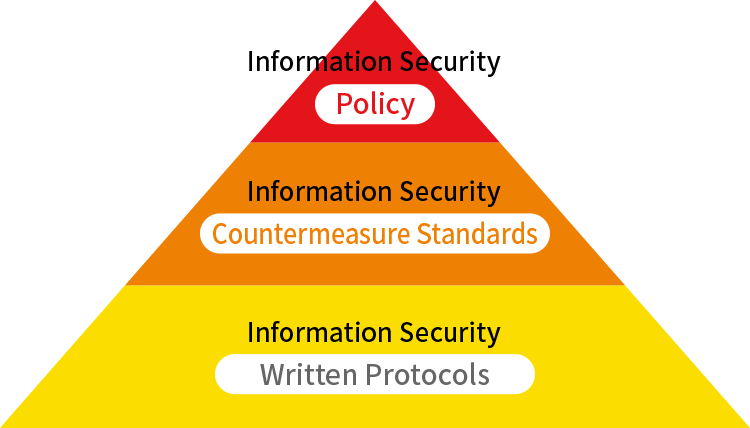
Risk management for information security is an important issue in business. We have established an Information Security Policy to facilitate protection and management of information handled in-house and information assets such as computers and networks. Our “Information Security Policy” consists of rules for protecting and managing our information assets to prevent falsification, destruction, leaking, etc. irrespective of whether it is deliberate or accidental. We have created specific standard rules and written implementation protocols grounded in a basic policy and ensure that all employees comply with these to the letter.